In which TCP attack is the cybercriminal attempting to overwhelm a target host with half-open TCP connections?
- reset attack
- port scan attack
- SYN flood attack
- session hijacking attack
The correct answer is SYN flood attack.
Understanding TCP Attacks: Tools, Techniques, and Real-World Examples
Cyberattacks exploiting the TCP (Transmission Control Protocol) are significant threats to networked systems, with varying objectives such as service disruption, unauthorized access, or reconnaissance. In this article, we delve into four common TCP-based attacks: SYN Flood, Reset Attack, Port Scan, and Session Hijacking. We’ll explore the tools attackers use, real-world examples, and their broader impacts.
1. SYN Flood Attack
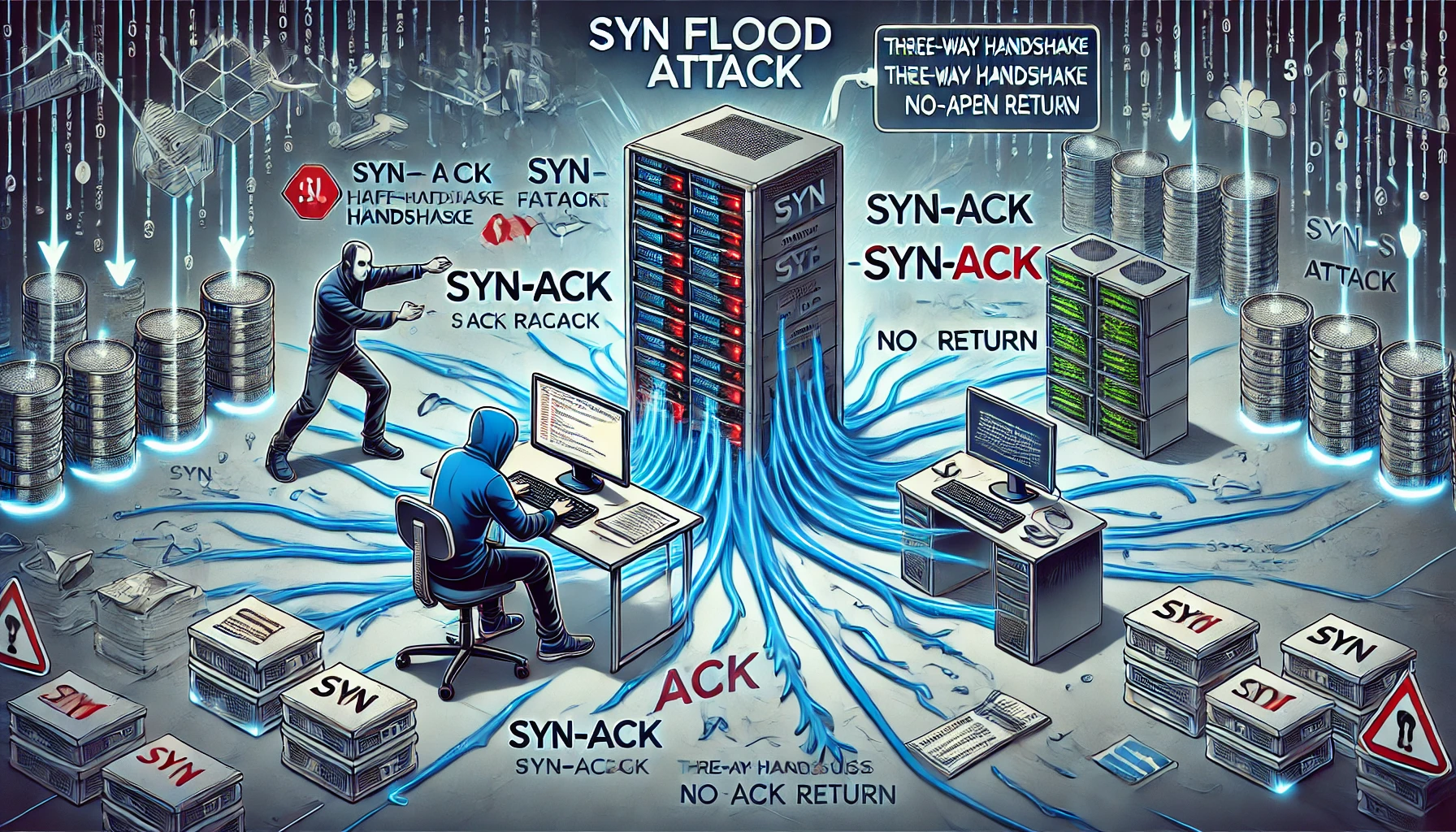
How It Works
A SYN flood attack exploits the three-way handshake of the TCP protocol:
- Attacker Sends SYN Packets: Numerous TCP SYN (synchronize) requests are sent to a target.
- Target Responds with SYN-ACK: The server allocates resources for each connection.
- No Completion of Handshake: The attacker does not send the final ACK packet, leaving connections half-open.
By overwhelming the server with these incomplete connections, legitimate requests are denied service.
Tools Used for SYN Flood
- Hping3: A packet crafting tool capable of generating SYN packets at high rates.
- LOIC (Low Orbit Ion Cannon): Often used in distributed attacks to flood a target with TCP SYN packets.
- Metasploit Framework: A comprehensive penetration testing tool with modules for SYN flood simulation.
Real-World Example: GitHub Attack (2018)
In 2018, GitHub experienced one of the largest Distributed Denial-of-Service (DDoS) attacks, peaking at 1.35 Tbps. Although this specific incident involved amplification techniques, SYN flood attacks are often a component of such large-scale disruptions.
Impact
- Downtime: GitHub’s service was temporarily disrupted, impacting millions of developers relying on the platform.
- Financial Loss: Downtime costs can be significant for businesses depending on online operations.
- Mitigation Costs: Deploying mitigation measures like CDNs and advanced firewalls incurs additional expenses.
2. Reset Attack
How It Works
Reset attacks exploit TCP’s connection termination mechanism:
- The attacker observes or guesses TCP session details (e.g., IP addresses and port numbers).
- Forged TCP packets with the RST (reset) flag are sent to the target, forcing it to close the connection.
Tools Used for Reset Attacks
- Scapy: A Python-based tool for crafting and sending custom packets.
- Netwox: A versatile toolset for packet crafting and injection, including TCP RST packets.
Real-World Example: Cisco Router Reset Exploit (2007)
Attackers exploited vulnerabilities in Cisco routers by sending malicious TCP RST packets to disrupt Border Gateway Protocol (BGP) sessions. This attack temporarily disrupted internet traffic routing, highlighting the potential for widespread network disruption.
Impact
- Network Disruption: Disruption of BGP sessions affected traffic routing across ISPs.
- Loss of Trust: Repeated disruptions can erode confidence in service providers.
- Cost of Recovery: Resolving such issues requires time, expertise, and financial resources.
3. Port Scan Attack
How It Works
Port scanning is a reconnaissance technique to discover open ports and services on a target system:
- The attacker sends packets to multiple ports on the target.
- Based on responses, the attacker identifies open ports and running services.
- This information is used to plan further attacks.
Types of Port Scans
- SYN Scan: Sends SYN packets without completing the handshake.
- UDP Scan: Tests UDP ports by sending empty packets.
- XMAS Scan: Sends packets with unusual flags to analyze system responses.
Tools Used for Port Scanning
- Nmap: A widely used network scanning tool for detecting open ports and services.
- Masscan: A high-performance scanner capable of scanning the entire internet in minutes.
- Angry IP Scanner: A simple tool for scanning IP addresses and ports.
Real-World Example: SolarWinds Breach (2020)
Before infiltrating systems via malicious software updates, attackers used sophisticated reconnaissance, including port scanning, to identify exploitable services.
Impact
- Pre-Attack Intelligence: Port scanning helps attackers pinpoint vulnerabilities.
- Unauthorized Access: Open ports with outdated or unpatched services provide easy entry points.
- Regulatory Penalties: Organizations may face fines for inadequate security measures.
4. Session Hijacking Attack
How It Works
Session hijacking involves taking over an active session between two parties by impersonating one of them. It often targets HTTP, HTTPS, or other session-based protocols:
- Session Interception: The attacker intercepts session tokens or identifiers (via sniffing or exploiting weaknesses).
- Session Injection: Using stolen session tokens, the attacker gains unauthorized access to the system.
Tools Used for Session Hijacking
- Ettercap: A tool for network traffic interception and analysis.
- Burp Suite: A professional penetration testing tool for analyzing and manipulating HTTP sessions.
- Wireshark: A network protocol analyzer capable of capturing and examining session traffic.
Real-World Example: Firesheep (2010)
The Firesheep browser extension demonstrated how easy it was to hijack unencrypted HTTP sessions over public Wi-Fi networks. By capturing cookies, attackers could impersonate users on social media platforms like Facebook and Twitter.
Impact
- Data Theft: Hijacked sessions provide attackers access to sensitive data, such as personal information or financial details.
- Identity Theft: Attackers impersonate users to perform malicious actions or steal credentials.
- Reputation Damage: Compromised accounts can be used for fraudulent or harmful activities.
Comparative Analysis of TCP Attacks
| Attack Type | Goal | Tools | Impact |
|---|---|---|---|
| SYN Flood Attack | Overwhelm server resources | Hping3, LOIC, Metasploit | Server downtime, financial loss, disrupted business operations. |
| Reset Attack | Disrupt ongoing connections | Scapy, Netwox | Network disruption, loss of trust, and expensive recovery processes. |
| Port Scan Attack | Reconnaissance | Nmap, Masscan, Angry IP Scanner | Identification of vulnerabilities, unauthorized access, regulatory fines for inadequate security. |
| Session Hijacking Attack | Take over a user session | Ettercap, Burp Suite, Wireshark | Data theft, identity theft, reputation damage, and potential regulatory penalties for compromised systems. |
Mitigation Strategies Across Attacks
- Firewalls: Configuring firewalls to block suspicious or unauthorized traffic.
- Intrusion Detection Systems (IDS): Deploying tools to detect and respond to unusual network activities.
- Encryption: Ensuring communication channels (e.g., HTTPS) are encrypted to protect sensitive data.
- Session Management: Implementing secure tokens, session timeouts, and invalidation mechanisms.
- Rate Limiting: Restricting the number of requests per client to prevent resource exhaustion.
- Patch Management: Regularly updating software to address known vulnerabilities.
Conclusion
TCP-based attacks like SYN floods, reset attacks, port scans, and session hijacking highlight vulnerabilities inherent in the protocol’s design. Cybercriminals leverage sophisticated tools to execute these attacks, causing significant disruptions, financial losses, and reputational damage. Real-world incidents, such as the GitHub DDoS attack and the Firesheep session hijacking case, underscore the importance of proactive security measures.
Organizations must adopt a multi-layered defense strategy, combining robust network architecture, up-to-date tools, and comprehensive monitoring, to mitigate these threats effectively. Understanding these attacks and their impact is critical for enhancing the resilience of modern networks.


